
12 May User Login Alert
In this blog, We can Discuss how to generate User Login Alert when an unauthorized user attempts to log in
The objective here is to generate a Login alert when an unauthorized user attempts to log in. So, an alert will be generated in Splunk when a user with wrong credentials attempts to log in to your windows PC. These alerts, in general, helps to monitor and respond to particular events. They search for real-time events or schedules using a saved search. Hence, an alert triggers when search results match with specific conditions. When alerts trigger, one can use alert actions to react.
A real-time alert explores incessantly for real-time results. Every time a result matches the specific trigger condition, you can configure the alerts in real-time to trigger.
Procedure:
- Install Splunk Universal Forwarder package on remote windows PC (PC1)
- Gather windows event logs on PC1
- Move the above-mentioned logs from PC1 to PC2, where data gets indexed on Splunk Indexer.
- Now, an alert is to be created on the PC2 Splunk instance.
Configuration of Splunk Universal Forwarder:
Host Name: ACi25N
To gather Windows Events Logs, add the inputs.conf file mentioned below to Universal Forwarder (PC1), or create one with the following.
(Path: $Splunk_Directory$\Splunk\etc\system\local)
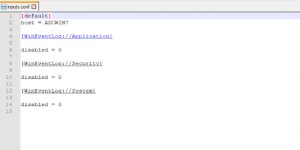
Now, to move this data to PC2, add outputs.conf to Splunk Universal Forwarder (PC1), or create with the following.
(Path: $Splunk_Directory$\Splunk\etc\system\local)
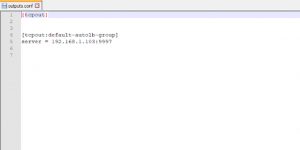
Configuration of Splunk Indexer:
Host Name: ACI3NEWP
To acquire the data from Forwarder, add inputs.conf to Splunk Indexer, or simply create with the following.
(Path: $Splunk_Directory$\Splunk\etc\system\local)
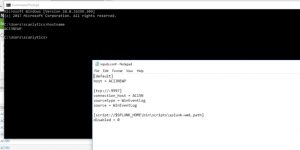
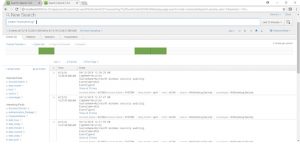
To check if the data is getting indexed to the indexer or not, open Splunk Indexer instance.
Query: index=”wineventlog”
Now, generate a lookup file with fields named Host_Name and User_Name, which has only the values of PC1 and PC2.
The picture below shows a lookup file with details of the users, authorized to use respective host
Query: |inputlookup logon
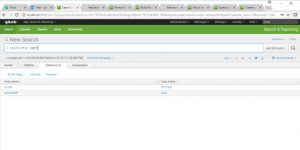
Now execute the following query in which we are going to set an alert:
Index=”wineventlog”Account_Name!=”$”|eval temp=mvindex(Account_Name,-1)|lookup logon Host_Name as ComputerName|eval Status=if(temp=User_Name,”1”,”0”)|table ComputerName temp User_Name Status

The result is saved as Alert

If you have any queries feel free to post them in the Comment Box below and for more interesting topics follow us on 👍 Social Networks, Happy Splunking




